Blocking and tackling to maintain primary level of defense.
We guide business and Information Technology executives and help them identify and remediate their cyber threats. We help them baseline their existing security program and enhance its maturity level by aligning their security strategy to their technology strategies as well as business objectives. In short, we provide a defense in depth layered cyber strategy and technology implementations to address evolving threats.

Risk Assessment
Enterprises in every industry and of all sizes are finding themselves under an increasing barrage of cyberattacks. At the same time, the threat landscape is evolving, becoming more sophisticated and doing so at a faster pace than many organizations are able to keep up with. Microbase’s risk assessment methodology goes beyond the standard audit or information security assessment. We strategically focus on controls within your business functional areas that will help you enhance your overall information security posture. We evaluate processes, technologies and current program maturity level from a security perspective – based on the NIST Cyber Security Framework:
NIST Cyber Security Framework
- Identify : First step is to recognize the risks affecting your assets, systems, data, and capabilities by understanding the environment so that you can manage these risks effectively.
- Protect : Second step is to develop and implement appropriate safeguards to minimize the impact if a cyber breach occurs
- Detect : Third step is to implement appropriate measures to detect cybersecurity events.
- Respond : Fourth step is to contain and minimize the impact of a cybersecurity event, should it occur.
- Recover : Final step is to develop and implement effective processes to restore any capabilities or services that were impacted by a cybersecurity event.
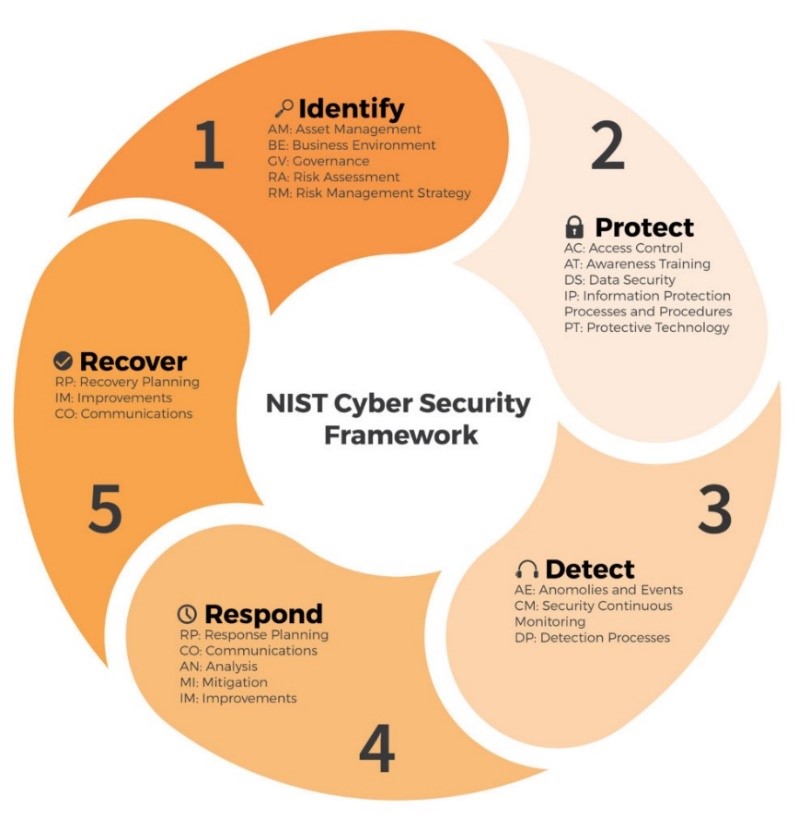
Simply put, we use the NIST Cyber Security Framework to provide a strategic view of the information security risk management lifecycle of an organization. The deliverable of the Risk Assessment is your organization’s maturity level across 22 categories of risks.
Strategy & Roadmap
A strategy is critical to the success of an information security program by providing a long term view and by guiding the execution of various initiatives. Microbase develops a tailored strategy based on the current risk assessments and guided by business and Information Technology objectives. We design the strategy around the customer’s needs to enhance their business opportunities, ROIs, and regulatory compliance.We help your organization in developing its roadmap in context with your priorities and existing plans while recommending an executable sequence for implementing them. This includes a Gantt chart of the proposed roadmap and descriptions of how each recommendation affects your overall maturity and the factors involved in implementing them.Our phased approach helps ensure an effective and efficient strategy that leverages NIST Cyber Security Framework and can be mapped to a number of cyber regulations (e.g., PCI, HIPAA, GDPR, and NYDFS) and industry best practices (CIS Top 20 Controls).
Awareness & Training
Employees and contractors are a major attack surface of any organization. For that matter, Awareness & Training is an essential part of a company’s security program to ensure that users have the required know-how to defend themselves as well as their organization against any potential threats. To be compliant with various industry and government regulations, such as HIPAA, PCI, FISMA, or Sarbanes-Oxley, you must invest in getting your employees and contractors appropriate security awareness training.Microbase offers an outstanding security awareness program that educates your employees and contractors about corporate policies and best practices. Users are trained about who to identify and report a security threat and are taught that data is a valuable corporate asset. Organizations need to tailor its Awareness & Training program to the specific needs of various groups to be effective. The program should address all stakeholders, including leadership, employees, contractors, and external service partners.Microbase recommends and helps implement training on topics targeted at various groups within your organization, as needed. This can range from the highly technical (e.g., secure coding practices) to general data handling. We can also oversee controlled ethical phishing campaigns to raise security awareness levels among employees and contractors.
Security Solutions
With the ever-increasing rate and diversity of threats, detecting and analyzing cyber threats is becoming a challenge. In addition, conventional detection and blocking methods are failing to mitigate these threats.Cybersecurity technology solutions must continually adapt as technologies and threats evolve. It is a challenging task to remain updated on current trends and evolving threats. However, this must remain a main objective for information security teams.We help you anticipate, identify, and implement technology solutions to reduce your exposure with adaptable defenses. Microbase provides your team with expert guidance, design recommendations, assistance in the selection process, and implementation for the following cybersecurity defense in depth layers:
- Cloud Security : We use a set of policies, controls, procedures and technologies that work in coherence with one another to protect cloud-based systems, data, and infrastructure in a Shared Responsibility Model between client and cloud vendor.
- Web Application Security : We protect your online services and websites against any security threats that target the vulnerabilities in your web applications.
- Database Security : We secure your databases using access controls, encryption, and timely detection of “suspicious database queries.
- End Point Security : : We address the risks presented by devices connecting to your network such as mobile devices, laptops, and desktop.
- Email Security : We use latest techniques for securing and keeping sensitive information in email communication secure against unauthorized access, loss, or compromise.
- Infrastructure Security : We implement policies and practices that prevent and monitor unauthorized access, misuse, modification, or denial of services for your network-accessible resources.
- Identity & Access Managementy : We We help organizations in the implementation of policies and technologies for ensuring that your users have the appropriate access to technology resources.
- Vulnerability & Patch Management : We identify and remediate vulnerabilities within your infrastructure and applications which could be exploited by attackers.
- Threat Management & Incident Response : We identify, analyze security threats in real-time, and mitigate these threats.